Examples of Contingency Plan for Network Failure
When crafting a contingency plan for network failure, you should consider several key components. Start with clear documentation outlining response procedures for hardware malfunctions, software bugs, and human errors. Prioritize risks by evaluating their likelihood and impact. Include regular training sessions to prepare your team for these scenarios. You might reference real-world incidents, like the […]
The Contingency Planning Guide
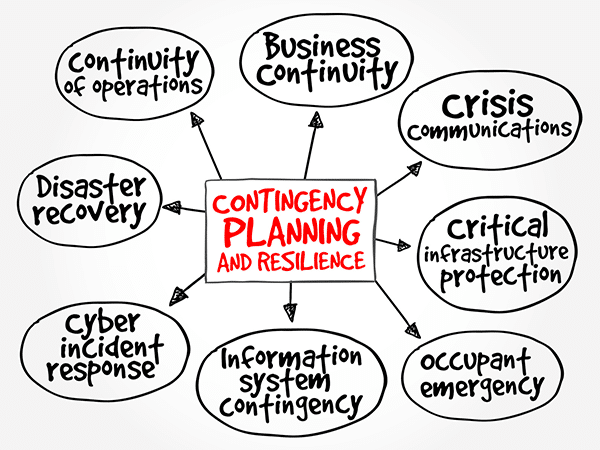
Sometimes a contingency plan (sometimes called a “Plan B”) is developed in case your chosen course of action doesn’t work out. A contingency planning guide is also a component of disaster recovery, business continuity scenarios and risk management that are part of nearly all business planning. Like this article mentions, a contingency plan is a course […]
How to Backup Data on your Android Device in 2022

Restoring data on Android device can be a lifesaver. It can be done directly from your phone to a Google account. You need to know the proper steps to backup data in order to protect valuable information. The data restoration process is different for various Android phones and versions. Let’s check out how phone data is stored: […]
Disaster Recovery Services Every Florida Business Needs

Massive data loss can destroy a business. Ransomware, fires, floods, and physical theft are just a few of the ways that your data could be wiped out. The irrecoverable loss of business records is worse than any physical loss. Insurance can cover the harm to furniture, equipment, and even an entire office, but it can’t […]
6 Cyber Security Must-Haves for Remote Work

The quick transition to remote work that many companies have had to make has revealed security risks that IT professionals are not able to monitor or correct as closely as they would be able to when employees work in-house. To mitigate these risks and protect data, employees will need to follow cyber security best practices […]

